The equipment of Tiangong Technology can be widely used in various data recovery laboratories, data analysis institutions, education platforms, big data room, command and dispatch center, multimedia data center and many other scenarios. It is the designated data source recovery technology “efficiency source technologyâ€. Equipment appearance supplier. The following is the specific application of the "Data Analysis All-in-One ED-MD9200" in the efficiency source technology data recovery service.
Equipment Name: Multi-function maintenance workstation ED-SP9600
Function introduction: Multi-function maintenance workstation ED-SP9600, with unique dual-screen display, technology blue environment lighting, full metal texture combined design; a variety of data interfaces, can integrate a variety of data analysis and repair equipment on the market It is equipped with Japanese white welding station, hot air gun, BGA welding machine, etc., and completes all kinds of equipment maintenance and data processing work in one stop. Product design professional, strong sense of science and technology, image atmosphere and anti-static, anti-electric shock and so on. Widely used in laboratory repair stations, various types of electronic equipment maintenance, computer city data recovery, command center integrated computer.
Equipment pictures:

[Editor's note: "Technology Combat" entered the second series of "Mobile Data Extraction", based on the real case of efficiency source in assisting public security organs to combat crime, combined with SPF9139Pro smart phone data recovery forensics platform (hereinafter referred to as "SPF9139" Equipment") and other equipment, explain the practical methods and techniques of mobile phone data extraction in the process of electronic forensics or forensic identification. Today, I will explain the first mobile phone case and fully present the most basic “mobile data extraction†process and basic precautions. Beginners of mobile data extraction can grasp the basic theory and practical methods through this article, and lay the foundation for the difficult data extraction and analysis in the next step. Because this case involves the detection of cyber fraud cases, all sensitive information in the text is blurred. 】
Case background: On the xx x day of 201x, the victim Zhou reported to the public security department of xx city that he was defrauded. In the process of investigating the case, the Criminal Police Brigade of xx City Public Security Bureau found that the suspect, Cao, by phone, WeChat, QQ, etc., after receiving the trust of the victim, sent a false photo to the victim and used the love as a cover to defraud the victim. Finance. To this end, the public security organs need to fix and extract the electronic data in the mobile phone of the criminal suspect, and provide evidence for combating crime.
Actual combat object: Android brand mobile phone, has Root, the appearance is intact (no slamming, soaking water, etc.), normal use, data is not deleted, need to extract telephone, WeChat, QQ and other communication information.
Technical analysis: Since the mobile phone is already Root, the data extraction of such mobile phone information is of a conventional type. The basic process of the efficiency source SPF9139 system - "physical image", "data extraction", "data analysis" and "generate report" can be completed (Figure 1).
Figure 1: SPF9139 system business operation process
Extraction equipment:
SPF9139 system is a comprehensive system integrating data extraction, recovery and forensics analysis of smartphones. It can be applied to computers or multiple hardware platforms (computers or workstations) according to actual needs. This case uses a workstation equipped with SPF9139 system (Figure 2). In addition to data recovery, extraction, forensic analysis and other functions, it can also extract mobile phone chips and play an important role in combating cybercrime.

Figure 2: Workstation with SPF9139
Extraction steps:
First, preliminary preparation
1. Mobile phone signal shielding. As soon as the mobile phone is turned on, it will automatically communicate with the outside world, which may cause the mobile phone information to be tampered with. Therefore, in the process of electronic forensics or forensic identification, it is necessary to use a signal shielding device (as shown in Figure 3) to avoid data changes caused by the communication between the mobile phone and the outside world, and to ensure the integrity and originality of the data of the mobile phone.

Figure 3: The phone is loaded into the shielding bag
2. The mobile phone is connected to SPF9139. Connect your phone to a computer or workstation equipped with the SPF9139 system via a data cable. Due to the large number of data lines, but not all data lines have data transmission functions, so it is necessary to use the original data lines as much as possible (non-original may cause connection failure, affecting the efficiency of forensics). At the same time, the data line interface of the computer or workstation port should be “read-only†to prevent the computer from changing the data in the mobile phone to ensure the integrity and originality of the forensic data.
3. Start the SPF9139 system. Start SPF9139 through the computer or workstation operation interface (see Figure 4), the system will automatically read and display the basic information of the phone, such as mobile phone brand, mobile phone model, mobile phone system, root or so. According to the interface prompt, the mobile phone in this case has been Root (Figure 5).
Figure 4: Starting the SPF9139 system
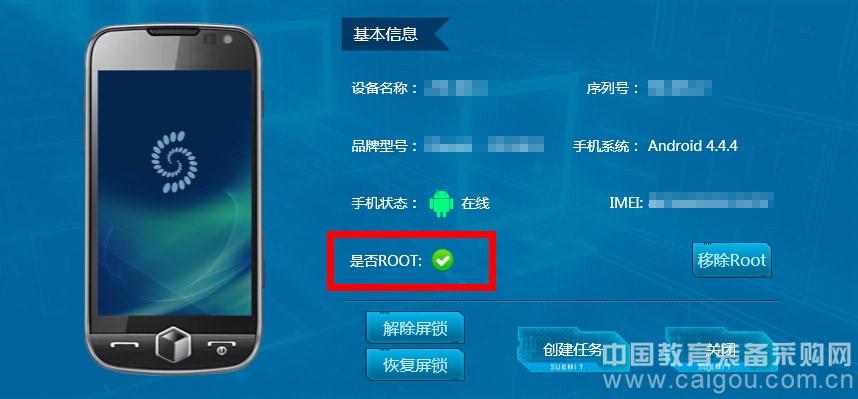
Figure 5: SPF9139 system detects that the phone has been Root
4. Create a mobile phone extraction task. Click the "Create Task" button to fill in the information related to the case, including the task name, the case, the mobile phone brand, the phone model, the inspector, the inspection time, etc. (The content of the case belongs to the confidential information, all of which are mosaic processed, as shown in Figure 6. ), after the convenience, quickly query the case.
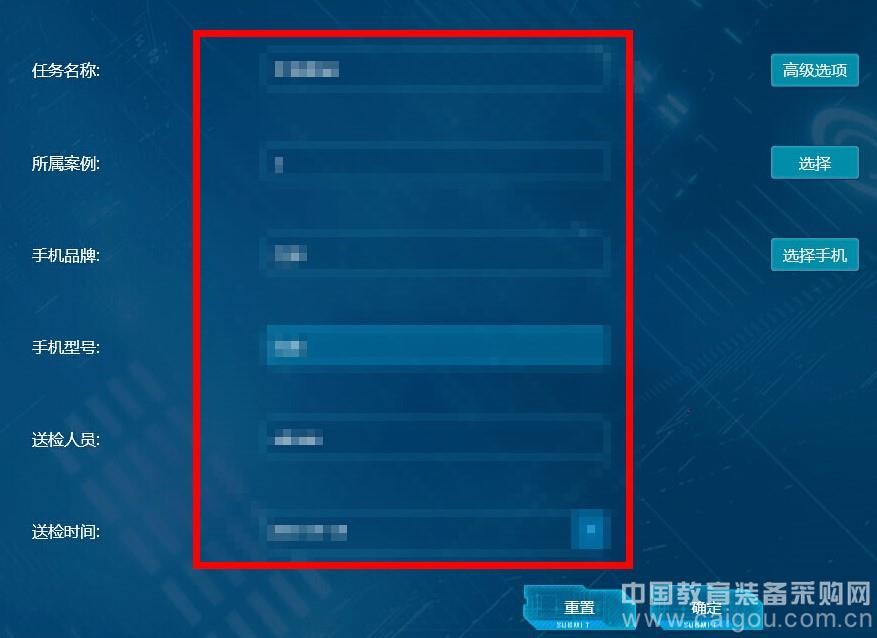
Figure 6: Create a new task (fill the basic information in a red box)
Second, the physical image
The so-called physical mirroring refers to copying the information data of the extracted object. According to the "General Principles of Judicial Authentication Procedures", judicial appraisal generally cannot be operated directly on the inspection materials (subject to inspection), but requires operations on the copy. For electronic forensics, data recovery, etc., in order to ensure data security, it is also recommended to extract and analyze on the image file.
As shown in Figure 7, the left side of the physical image page is the "mirror source", which is the object of extraction (the mobile phone of this case). You can select the mobile phone, SIM card, and SD card according to your needs. Under each item, you can also select a specific area. Includes all memory chips, data area, system area, and buffer area. In order to ensure the integrity of the evidence, the case selected is "all mobile phone memory chips." On the right is the "mirror target", which is the image file storage address, you can choose the default address (C:\XLYSFTasks\filename\mirror,), or you can specify it yourself.
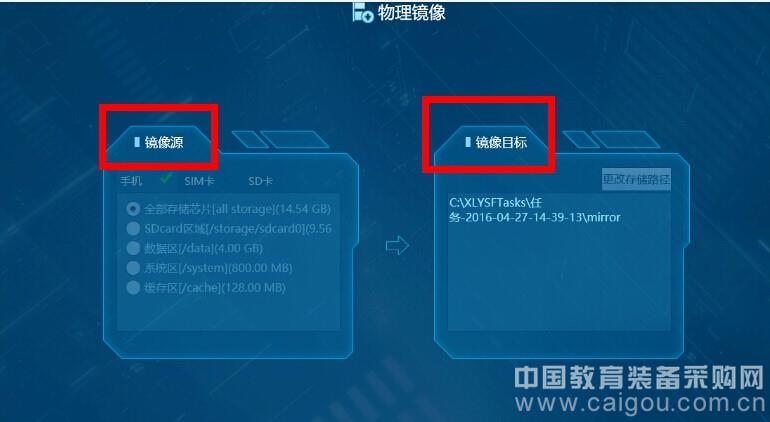
Figure 7: Selecting the physical source and mirror target
Third, data extraction
1. Load the physical image file. After the physical mirroring is successful, create a new task (as shown in Figure 8). The “task name†can fill in the data information category that needs to be extracted (when it is convenient to distinguish which part of the data is later), if this case can be filled in as “** mobile phone call record, WeChat , QQ extraction". After completing the new task, go to the data extraction page (Figure 9) and select the “Mirror Load†button (Figure 10). Find the physical image storage location (C:\XLYSFTasks\filename\mirror) of this case and load the physical image.
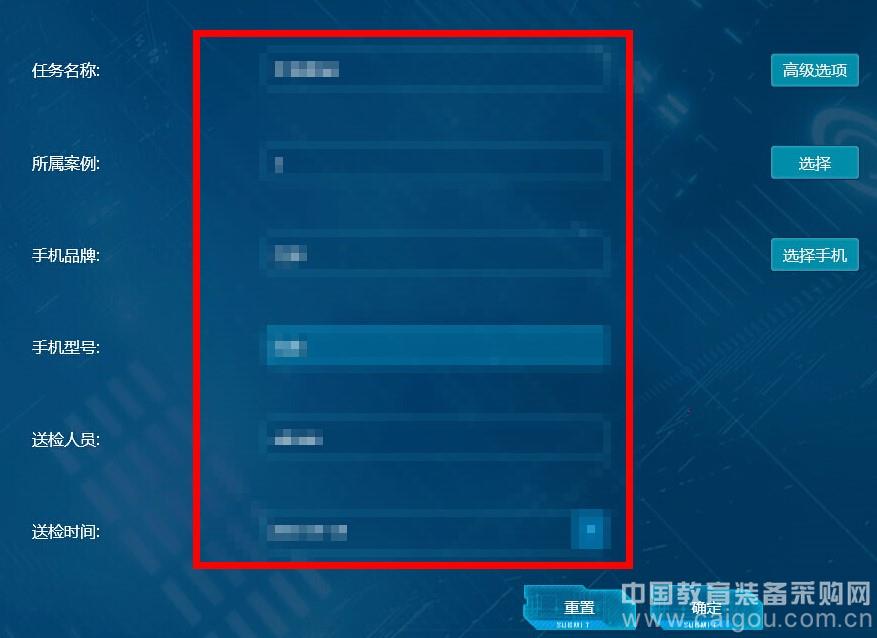
Figure 8: Creating a new data extraction task

Figure 9: Click to enter the data extraction page
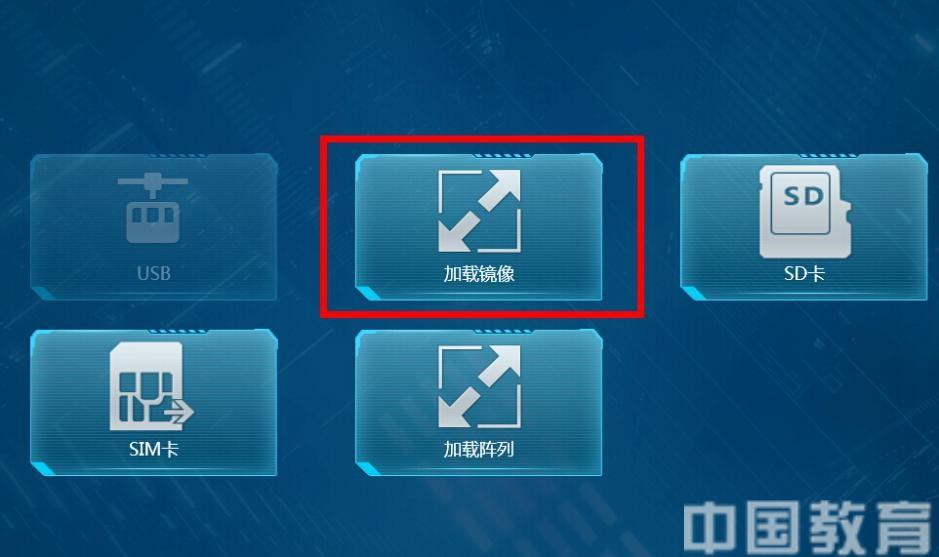
Figure 10: Select to load the image
2. Select the category you want to extract. The data that the SPF9139 system can extract includes most of the mobile phone applications such as address book, call history, text message, social chat, mainstream mailbox, and map bus. According to customer needs, this case only selects telephone, WeChat, QQ and other communication methods (Figure 11, 12).
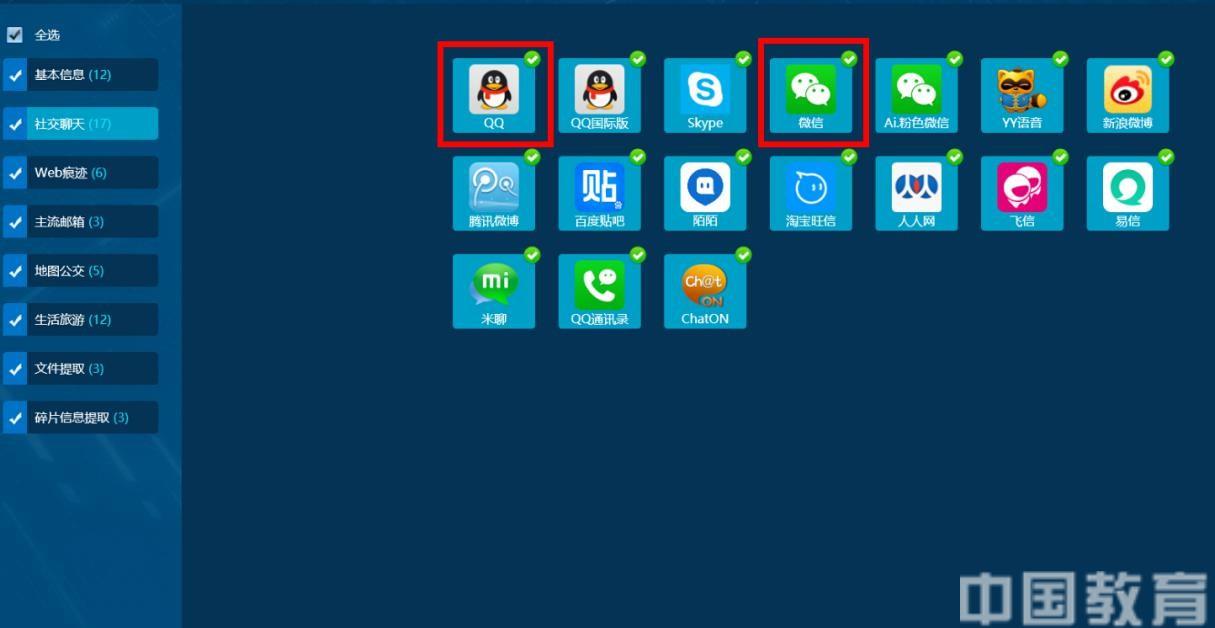
Figure 11: Selecting and extracting QQ and WeChat data
Figure 12: Selecting and extracting call history
3. Extract mobile phone data. Click the “Start Extract†button to extract the relevant information data you need (Figure 13).
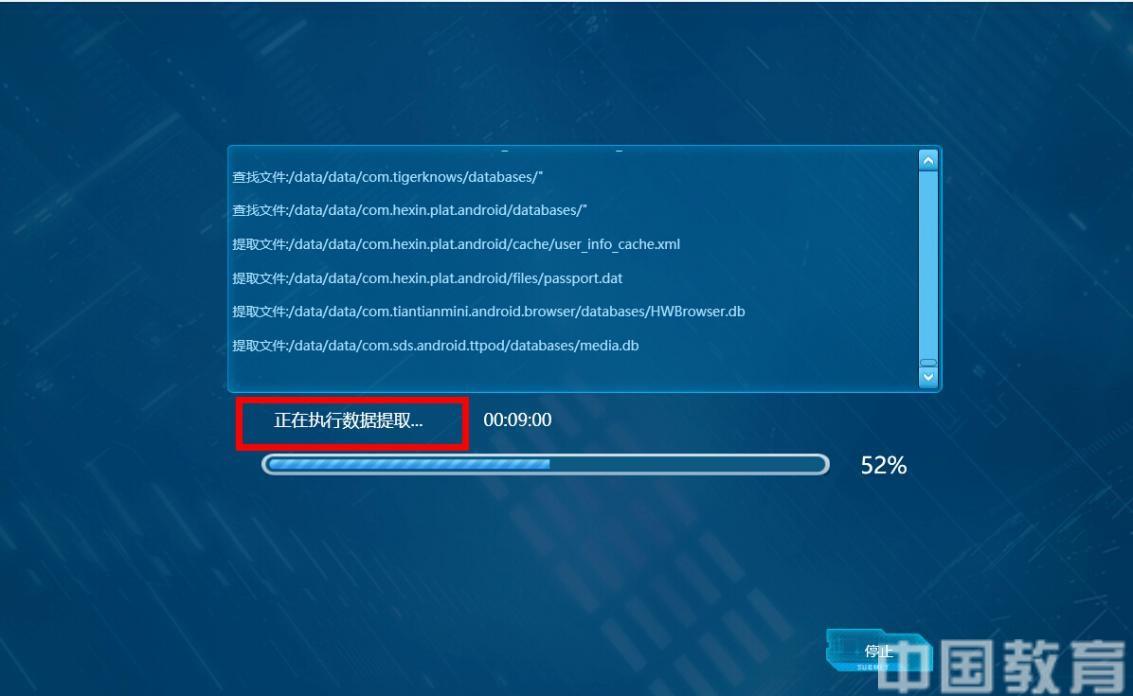
Figure 13: Data Extraction
Fourth, analyze the extracted data
After the data is extracted, the SPF9139 system automatically enters the data analysis page. Click on WeChat, QQ, Phone, etc. to extract the catalogue, and perform detailed data analysis on each item. For example, in this case, clicking the mobile phone call record can clearly display the contact, the time of the call, the duration of the call, the attribution of the number, the distribution of the call number, the frequency of the call, etc., thereby locking the target number information to be extracted (see Figure 14). The data extraction of WeChat and QQ is the same.
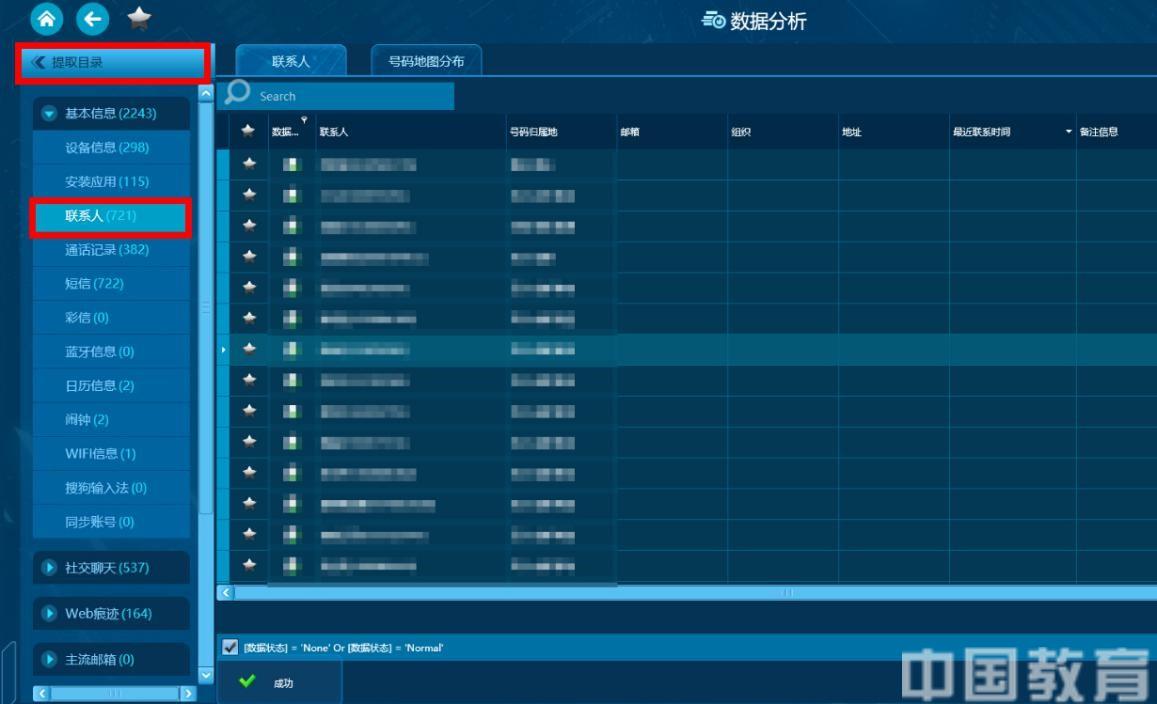
Figure 14: Analyze phone call history
Fourth, export data analysis report
After analyzing the extracted data, the corresponding extracted data information can be generated into an analysis report according to the needs of the case, and the results of the data extraction are fully presented for the case to be detected or forensic.
Extraction results: Through the above five major steps, the external communication records and data of the mobile phone are extracted and fixed, which provides evidence for the rapid detection and judicial judgment of the case.
Note: 1. When carrying out data extraction, be sure to put the phone into the signal shielding bag first.
2, in order to improve the efficiency of evidence collection, try to use the original data line.
3. When performing data extraction analysis, be sure to use a physical image.
[Editor's post: In the process of electronic forensics and judicial appraisal by the public security and the judiciary, it is often necessary to fix and extract the electronic data in the Android ROOT mobile phone. Through this case, we can see that the efficiency source SPF9139 smartphone data recovery forensics system can easily create mirrors and analyze and extract data. On how to carry out non-ROOT extraction of Android mobile phones, IOS jailbreak extraction, IOS non-jailbreak extraction, chip data extraction of damaged mobile phones, bypassing Android screen locks, ROOT permissions, etc. will be presented for you in future cases, so stay tuned! 】

Synthetic ponytail extension is a clip-in long wavy curly large volume fluffy hair, perfect for girls, lady, black woman to add your hair volume or change the style immediately.
The ponytail extension is made from premium synthetic fiber with matte finish. Soft and natural like human hair. It works with different hair lengths and can clip into thin or thick hair.
Create a high ponytail, a face ponytail, or just simply add the ponytail hairpiece for a different hairstyle. You can cut it shorter or thin it out. It can be also straightened or curled.
The tangled problem can be solved by mixing ponytail with vinegar, baking soda and water and soaking it with some conditioner.
The ponytail extension simply clips above a hair tie and adds a ponytail to your real hair. Just insert the clip above the hair tie and wrap your hair with the wide soft weft and use bobby pins if needed to keep in place.
Like all synthetic hairpieces, static & humidity may cause the ponytail extension to tangle. By using hair softening products to keep the texture of the clip-in ponytail smooth. If it becomes tangled, brush it from the bottom of the ponytail using a wide comb.
Synthetic Ponytail,Slicked Back Ponytail,Drawstring Ponytail,Synthetic Curly Ponytail
Xuchang Le Yi De Import And Export Trade Co., Ltd. , https://www.lileaderbeauty.com
![<?echo $_SERVER['SERVER_NAME'];?>](/template/twentyseventeen/skin/images/header.jpg)